Build an Agentic AI SOC Analyst with Python for Threat Hunting (Video Course)
Build an AI SOC analyst that reads plain-English requests, hunts real logs with KQL, maps to MITRE ATT&CK, and can isolate a host via API. Learn just enough Python, prompts, and guardrails to shift from alert-chasing to reliable automation.
Related Certification: Certification in Building and Deploying Python Agentic AI for SOC Threat Hunting

Also includes Access to All:
What You Will Learn
- Build an agentic AI SOC analyst that turns plain-English intent into KQL and JSON findings
- Implement a two-call LLM workflow: intent derivation then deep cognitive analysis
- Write practical Python orchestrator code for LLMs, KQL queries, and remediation APIs
- Design and enforce guardrails: allow lists, PII redaction, time caps, approval gates, and token budgets
- Perform safe automated remediations (e.g., isolate hosts) with audit logging and confirmation flows
Study Guide
Cybersecurity, Python, & Threat Hunting w/Agentic AI (Full Course)
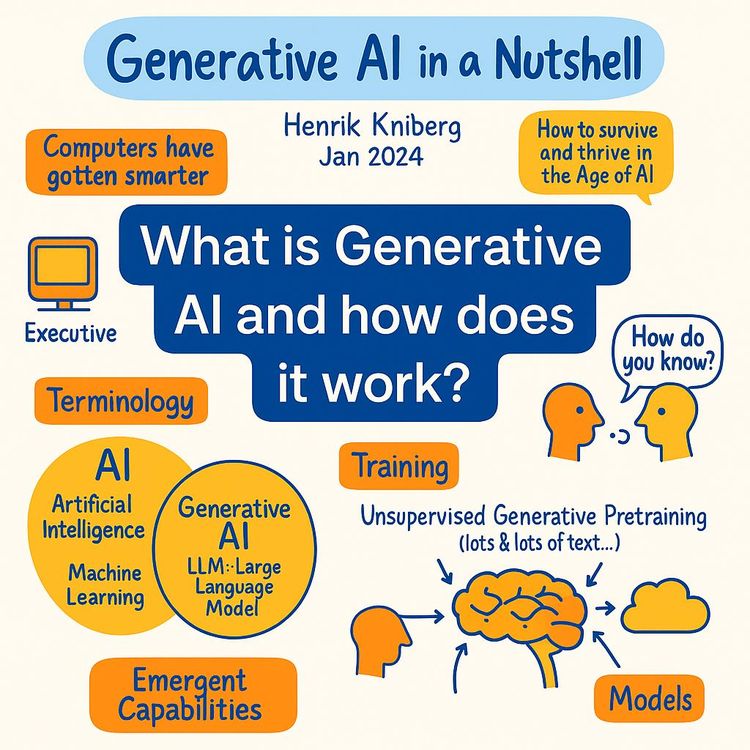
Let's build something that changes how you think about security work. This course teaches you how to go from zero to a working AI-powered SOC analyst,an agent that reads your intent in plain English, hunts through real logs, maps findings to MITRE ATT&CK, and can isolate a compromised host over an API call. You'll learn the Python that matters, the KQL you actually use, and the prompt engineering required to make AI useful instead of noisy.
Value? You'll stop playing whack-a-mole with alerts and start orchestrating autonomous systems that work at machine speed. This is the career upgrade: from manual analyst to AI orchestrator and builder. You'll understand how it all fits together,LLMs, tokens, SIEMs, JSON schemas, and remediation APIs,and you'll finish with a blueprint you can extend, ship, and own.
What You'll Build (and Why It Matters)
We're building an "Agentic AI" SOC analyst. It interprets your natural language request, determines the right log source and timeframe, fetches only the necessary data, performs a cognitive threat analysis, returns structured results (JSON), and,if warranted,executes a remediation like isolating a device. You orchestrate; the agent executes. Expect a full walk-through of the workflow, guardrails, cost controls, and safety checks.
Example outcome:
- You ask: "Check 'Windows-Target-1' for brute force activity in the last day."
- The agent chooses DeviceLogonEvents, queries KQL, analyzes signs of brute force, returns ATT&CK technique mapping and IOCs, then optionally isolates the device via Microsoft Defender for Endpoint.
Mindset Shift: From Manual Analyst to AI Orchestrator
Traditional Tier 1 workflows rely on manual triage and repetitive log pivots. Agentic AI removes the slog. It parses intent, handles data plumbing, and escalates with explanations and confidence. Your job becomes designing: prompts, policies, tools, and automated actions.
Key idea: AI in cybersecurity isn't just "better search." It's a closed-loop system that can observe, decide, and act,safely,faster than a human. Proper guardrails make it reliable; proper prompts make it sharp; proper APIs make it useful.
Example scenarios:
- "Was there any suspicious service creation on any domain controller overnight?" Agent chooses appropriate table(s), filters on service creation events, looks for rare service names, returns high-signal findings with ATT&CK mapping.
- "Scan for mass token failures followed by a successful sign-in from a new IP for user 'alex'." Agent selects SigninLogs, filters time window, correlates failures, flags suspicious success, and suggests next actions.
Core Concepts You Need (Quick Definitions)
- Agentic AI: An AI system that can perform a task and then take action on its own with minimal or no human input.
- AI SOC Analyst: An agent designed for log analysis, threat detection, reporting, and,optionally,remediation.
- Threat Hunting: Proactive searching for threats that evade controls; usually iterative and hypothesis-driven.
- LLMs: Language models that understand and generate text. They power intent parsing and cognitive analysis.
- Prompt Engineering: Designing instructions, context, and output schemas so the model delivers precise, structured results.
- JSON: Your agent's lingua franca. If it's not structured, you can't automate.
- KQL: Query language for Azure Log Analytics and Microsoft Sentinel.
- Token: Billing/processing unit for LLMs; both prompts and responses consume tokens.
- Guardrails: Rules and constraints that keep the agent safe, predictable, and on-budget.
Example mental model:
- Think "two LLM calls": first for intent → query parameters, second for deep analysis → structured JSON findings. The JSON drives reports and actions.
Python Fundamentals (What You Actually Need)
You don't need to be a software engineer to build an agent. You need practical fluency with a focused set of tools: variables, dicts, lists, functions, errors, and requests. Keep your code clean, composable, and explicit.
Example: Setup & key libraries
- Install Python and VS Code.
- pip install openai azure-monitor-query pandas requests python-dotenv tiktoken (or a similar token estimator).
- Use environment variables for secrets: OPENAI_API_KEY, AZURE_TENANT_ID, etc.
Example: Core Python patterns
# Variables and dictionaries
model_name = "gpt-4.1"
allowed_models = ["gpt-4.1", "gpt-4o-mini"]
threat = {"title": "Brute Force", "confidence": "high", "host": "Windows-Target-1"}
# Control flow
if threat["confidence"] == "high":
action = "isolate"
else:
action = "review"
# Functions
def estimate_cost(tokens, per_million):
return (tokens / 1_000_000) * per_million
# Error handling
try:
result = 1 / 0
except Exception as e:
print(f"Error: {e}")
Example: Keep your code modular
- One file for LLM utilities (prompt builders, API wrapper).
- One for KQL queries (templates and builders).
- One for remediation actions (Defender for Endpoint helpers).
- One for guardrails and config (allow lists, model caps).
- One for the main agent loop (orchestration).
APIs 101 for Security Builders
APIs are the nervous system of your agent. You'll call the LLM API, query a SIEM API, and hit remediation APIs. Respect auth, rate limits, and error handling. Always log requests and responses (sanitized) for traceability.
Example: OpenAI call (conceptual)
from openai import OpenAI
client = OpenAI()
resp = client.chat.completions.create(
model="gpt-4.1",
messages=[
{"role":"system","content":"You are a careful SOC assistant. Respond in JSON."},
{"role":"user","content":"Summarize ATT&CK T1059."}
],
response_format={"type":"json_object"}
)
Example: REST call to a security API
import requests
headers = {"Authorization": f"Bearer {token}"}
r = requests.post("https://api.securityprovider/isolate", headers=headers, json={"deviceId": "123"})
if r.status_code != 200:
print("Isolation failed:", r.text)
LLMs, Tokens, and Structured Output
The agent succeeds or fails on one thing: the LLM must return predictable, structured data. That's why we force JSON outputs and keep prompts tight. Token management keeps your costs under control and your responses within limits.
Example: JSON schema in the prompt
Please respond strictly in the following JSON format:
{
"threats": [
{
"title": "string",
"description": "string",
"confidence": "low|medium|high",
"mitre_attack_techniques": ["T####"],
"iocs": {"ips": [], "users": [], "hosts": []}
}
]
}
Example: Token optimization tips
- KQL-filter logs before sending to the LLM.
- Remove verbose fields; keep timestamps, principals, hosts, IPs, actions, outcomes.
- Cap response length with max tokens; request concise reasoning only when needed.
KQL Essentials You'll Actually Use
Most of the time, you're filtering by time range, entity, and action; summarizing counts; and joining to add context. Keep queries fast and tight. Send only what the LLM needs to reason effectively.
Example: Filter failed logons in the last 24h
DeviceLogonEvents
| where Timestamp > ago(24h)
| where DeviceName == "Windows-Target-1"
| where ActionType == "LogonFailed"
| summarize Failures = count() by AccountName, bin(Timestamp, 1h)
| order by Timestamp asc
Example: Sign-in anomalies by IP
SigninLogs
| where TimeGenerated > ago(24h)
| project TimeGenerated, UserPrincipalName, IPAddress, ResultType, Location
| summarize Success=countif(ResultType == 0), Fail=countif(ResultType != 0) by IPAddress, UserPrincipalName
| where Fail > 10 and Success > 0
Architecture: The Agentic AI SOC Analyst
Think in phases. Your agent moves in a predictable loop: understand, fetch, analyze, act. It's scripted, safe, and explainable.
- Phase 1: User Input & Intent Derivation
- Phase 2: Data Collection & Querying
- Phase 3: Cognitive Threat Analysis
- Phase 4: Structured Reporting & Automated Action
Example: Component map
- LLM for cognition (intent + analysis)
- Python orchestrator (glue code)
- SIEM/Log Analytics for data (KQL)
- Security platform APIs for action (e.g., Defender for Endpoint)
Phase 1: User Input & Intent Derivation
The agent takes a plain-English concern and converts it into a structured query plan: table, timeframe, entities, rationale. You supply a prompt "tools" map describing available tables and schemas.
Example: User prompt
"We heard about a new Azure enumeration utility. Anything unusual in the last day?"
Example: LLM output (intent object)
{
"table": "SigninLogs",
"timeframe_hours": 24,
"entities": {"users": [], "hosts": [], "ips": []},
"rationale": "Azure enumeration attempts often surface as unusual sign-in patterns. Start with SigninLogs."
}
Phase 2: Data Collection & Querying
Using the structured plan, the agent builds a KQL query and hits your SIEM. Optimization matters: narrow fields, narrow time. Keep results compact to respect token budgets.
Example: KQL template builder (conceptual)
def build_signinlogs_query(hours, user=None):
base = f"SigninLogs | where TimeGenerated > ago({hours}h)"
if user:
base += f' | where UserPrincipalName == "{user}"'
base += " | project TimeGenerated, UserPrincipalName, IPAddress, ResultType, AppDisplayName"
return base
Example: Cost-aware field selection
- Include: TimeGenerated, principal, IP, action, result, device/host.
- Drop: Long agent strings, verbose payloads, raw request bodies unless absolutely needed.
Phase 3: Cognitive Threat Analysis
This is where the LLM earns its keep. You assemble: original user request, table-specific hunting instructions, a strict JSON schema, and the filtered logs. The model returns findings with confidence, ATT&CK mappings, and IOCs.
Example: Table-specific instruction snippet
- For DeviceLogonEvents: "Look for unusual logon types, repeated failures followed by success, lateral movement patterns, logons outside normal hours, and new admin sessions."
Example: Returned JSON (simplified)
{
"threats": [
{
"title": "Credential Spraying on Windows-Target-1",
"description": "Multiple failed logons from 17 IPs over 4 hours, then a success.",
"confidence": "high",
"mitre_attack_techniques": ["T1110"],
"iocs": {"ips": ["203.0.113.10"], "users": ["svc-backup"], "hosts": ["Windows-Target-1"]}
}
]
}
Phase 4: Structured Reporting & Automated Action
The agent parses the JSON, renders a human-readable report, and (optionally) initiates remediation when confidence is high. Keep a confirmation step for sensitive actions unless policy allows autonomous execution.
Example: Confirmation prompt
"High-confidence threat detected (T1110) on Windows-Target-1. Isolate host? (y/n)"
Example: Posture-aware actions
- y → Isolate device via API; log ticket; notify channel.
- n → Leave in monitor state; attach recommended playbook steps.
Core Technological Components (Deep Dive)
- Large Language Models: The cognitive layer for intent and analysis. The briefing references names like GPT-4.1 and GPT-5; the idea is to select an appropriate, approved model from your allow list. Prompt engineering is not optional,it's the control surface of your agent.
- Python: The glue. You'll use openai (or compatible client), azure-monitor-query, pandas, requests, and a token estimator like tiktoken.
- Centralized Logs: Azure Log Analytics or a SIEM. You'll use KQL to pull targeted data.
- Security APIs: For action,e.g., Defender for Endpoint to isolate devices.
Example: Minimal orchestrator shape
- get_user_intent() → derive_query_plan()
- run_kql(plan) → logs
- cognitive_analyze(logs, schema, instructions) → findings_json
- maybe_remediate(findings_json) → API call(s)
Prompt Engineering That Actually Works
You'll write three types of prompts: a system message, a tools/context message, and a user request. Always define output schemas. Always constrain scope. Always add rationale when you need traceability.
Example: Intent derivation system prompt
You are an AI SOC planner. Given a user request and the allowed tables, return a JSON object: {"table": "...","timeframe_hours": int,"entities": {...},"rationale": "..."}. Use only allowed tables: ["SigninLogs","DeviceLogonEvents","DeviceProcessEvents"].
Example: Cognitive analysis prompt skeleton
- System: "You are a meticulous threat hunter. You must return strictly valid JSON per the schema."
- Assistant: "Table-specific hunting guidance: [insert]. Required schema: [insert]."
- User: "Original request: [insert]. Logs: [truncated, filtered]."
Guardrails: Non-Negotiable Safety and Reliability
The agent must never go off-road. Guardrails keep it on the approved path, manage cost, and protect data. Build these in code, not just prompts.
- Table/Field Allow Lists: Only query approved tables/fields.
- Model Allow List: Only approved models can be used.
- Time Window Enforcement: Hard cap (e.g., max 72h) unless explicitly overridden by a privileged operator.
- PII Redaction: Detect and remove sensitive fields before sending to an LLM; hash or mask values when needed.
- Action Permissions: Separate observe-only from act-capable modes. Require human confirmation or policy-based auto-approve.
- Rate Limiters and Budget Caps: Abort or degrade gracefully when nearing quotas.
Example: Guardrail check
if plan["table"] not in ALLOWED_TABLES:
raise ValueError("Table not allowed")
if plan["timeframe_hours"] > MAX_HOURS:
plan["timeframe_hours"] = MAX_HOURS
Example: Redaction stub
def redact_pii(records):
for r in records:
r["UserPrincipalName"] = hash(r.get("UserPrincipalName",""))
return records
Cost and Token Management (You'll Thank Yourself Later)
Tokens equal money. Prune your prompts. Summarize logs. Use cheaper models for intent parsing, heavier ones only when necessary.
Example: Token budgeting
- Estimate tokens with tiktoken; warn when a batch will exceed your threshold.
- Chunk logs by time or entity; iterate with running summaries to the model.
- Set strict response_format=json_object to avoid verbose prose.
Example: Pre-summarization
- KQL: summarize count by IP, user, hour. Then send those aggregates to the LLM first.
- If suspicious, fetch a focused slice of raw events for a second pass.
Building the Agent Step-by-Step (Code-Oriented Walkthrough)
We'll sketch the core modules you'll implement. Keep it simple and testable first; you can optimize once it works end-to-end.
Example: config.py
ALLOWED_TABLES = ["SigninLogs","DeviceLogonEvents","DeviceProcessEvents"]
ALLOWED_MODELS = ["gpt-4.1","gpt-4o-mini"]
MAX_HOURS = 72
Example: intent.py
from openai import OpenAI
client = OpenAI()
def derive_query_plan(user_text, allowed_tables):
system = "You are an AI SOC planner. Output valid JSON only."
tools = f"Allowed tables: {allowed_tables}. Return keys: table, timeframe_hours, entities, rationale."
resp = client.chat.completions.create(
model="gpt-4o-mini",
response_format={"type":"json_object"},
messages=[
{"role":"system","content":system},
{"role":"assistant","content":tools},
{"role":"user","content":user_text}
]
)
return resp.choices[0].message.content
Example: logs.py (Azure Monitor Query)
from azure.monitor.query import LogsQueryClient
from azure.identity import DefaultAzureCredential
credential = DefaultAzureCredential()
client = LogsQueryClient(credential)
def run_kql(workspace_id, kql):
return client.query_workspace(workspace_id, kql)
Example: analysis.py
def cognitive_analyze(logs_json, table_instructions, schema_json):
system = "You are a meticulous threat hunter. Output valid JSON only."
messages = [
{"role":"system","content":system},
{"role":"assistant","content":f"Instructions: {table_instructions}"},
{"role":"assistant","content":f"Schema: {schema_json}"},
{"role":"user","content":f"Logs: {logs_json}"}
]
resp = client.chat.completions.create(model="gpt-4.1", response_format={"type":"json_object"}, messages=messages)
return resp.choices[0].message.content
Example: actions.py (Defender for Endpoint)
import requests, os
def get_graph_token(tenant_id, client_id, client_secret, scope):
data = {"client_id": client_id,"scope": scope,"client_secret": client_secret,"grant_type": "client_credentials"}
r = requests.post(f"https://login.microsoftonline.com/{tenant_id}/oauth2/v2.0/token", data=data)
return r.json()["access_token"]
def get_device_id(token, device_name):
h = {"Authorization": f"Bearer {token}"}
r = requests.get(f"https://api.securitycenter.microsoft.com/api/machines?$filter=computerDnsName eq '{device_name}'", headers=h)
return r.json()["value"][0]["id"]
def isolate_device(token, device_id):
h = {"Authorization": f"Bearer {token}","Content-Type": "application/json"}
payload = {"Comment":"Automated isolation by AI agent","IsolationType":"Full"}
r = requests.post(f"https://api.securitycenter.microsoft.com/api/machines/{device_id}/isolate", headers=h, json=payload)
return r.status_code, r.text
Example: main.py orchestration
user_text = input("What should I investigate? ")
plan = derive_query_plan(user_text, ALLOWED_TABLES)
# validate and parse plan (JSON) …
kql = build_query_from_plan(plan)
rows = run_kql(WORKSPACE_ID, kql)
logs = redact_pii(parse_rows(rows))
findings = cognitive_analyze(logs, instructions_for(plan["table"]), schema)
print("Findings:", findings)
# If high confidence and host present → ask for confirmation → isolate
Case Study: Automated Isolation of a Compromised Host
Walk the full loop from concern to action.
1) Trigger: Analyst says, "I'm worried 'Windows-Target-1' was exposed and brute-forced in the last few days."
2) Analysis: Agent picks DeviceLogonEvents, filters last 72h, focuses on Windows-Target-1. LLM flags a brute-force pattern with high confidence.
3) Confirmation: "Isolate Windows-Target-1? (y/n)"
4) Action: If yes, get token → get Device ID → call isolate.
Example: KQL used
DeviceLogonEvents
| where Timestamp > ago(72h)
| where DeviceName == "Windows-Target-1"
| summarize Fails=countif(ActionType == "LogonFailed"), Success=countif(ActionType == "LogonSuccess") by bin(Timestamp, 1h), RemoteIP
| where Fails > 20 and Success > 0
Example: JSON finding drives action
{ "threats": [ { "title": "Brute Force", "confidence": "high", "iocs": { "hosts": ["Windows-Target-1"] } } ] }
Two LLM Calls: Why This Design Works
Call 1 (intent) reduces ambiguity. Call 2 (analysis) focuses cognition on context and logs. This separation keeps prompts small, reduces hallucination, and lets you tune model choice per step (cheaper model for intent, stronger model for analysis).
Example: Split-model strategy
- Intent: gpt-4o-mini (fast, cheap)
- Analysis: gpt-4.1 (more capable reasoning)
Example: Failure handling
- If intent returns an unapproved table, abort and ask the user for clarification.
- If analysis returns invalid JSON, retry once with a repair prompt, then fall back to a simplified schema.
Structured Output: The Contract Between AI and Action
Structured JSON is non-negotiable. It's how you go from "interesting" to "automatable." The schema acts like an API contract for your LLM.
Example: Required schema (expanded)
{
"threats": [{
"title": "string",
"description": "string",
"confidence": "low|medium|high",
"mitre_attack_techniques": ["T####"],
"iocs": {"ips": [], "users": [], "hosts": []},
"rationale": "brief string"
}],
"summary": "string",
"next_best_actions": ["string"]
}
Example: Parsing in Python
import json
data = json.loads(findings_json)
for t in data["threats"]:
if t["confidence"] == "high" and t["iocs"]["hosts"]:
print("Candidate for isolation:", t["iocs"]["hosts"][0])
Table-Specific Hunting Guidance (Playbooks the LLM Can Follow)
Provide clear, short hunting heuristics per table. This massively improves accuracy.
Example: DeviceLogonEvents guidance
- Look for: repeated failures followed by success, unusual logon types, new admin logons, rare times, lateral movement (logon to multiple hosts). Report users, hosts, IPs, counts.
Example: SigninLogs guidance
- Look for: impossible travel, MFA fatigue patterns, unfamiliar IP ranges, application-specific anomalies, location changes followed by privilege use.
Automated Actions: From Finding to Fix
Common initial actions: isolate endpoint, disable user, revoke sessions, block IPs, quarantine files. Each action should be gated by policy and confirmation rules.
Example: Isolation policy
- High-confidence host threat + non-critical environment → allow auto-isolation.
- Business-critical host → require human approval or safe-mode isolation (limited network segments).
Example: Adding "disable user" capability
- Implement Azure AD/Entra call: get user object → set accountEnabled=false.
- Enforce constraints: only service accounts in allow list or explicit approval for human users.
Cost Control: Practical Tips
- Use KQL to aggregate first; send summaries to the LLM; fetch detail slices only when needed.
- Streaming and chunking: break large log sets into small windows; request incremental judgments.
- Caching and reuse: reuse table instructions, schema, and even past summaries when appropriate.
Example: Chunk-then-judge
- Evaluate each 1-hour slice for anomalies; keep only suspicious slices for deep analysis.
- Merge results at the end into a single threat report.
Example: Budget guardrail
if projected_tokens > TOKEN_BUDGET:
return {"error": "Request too large. Narrow time or entities."}
Data Privacy and Governance
Sending logs to third-party models carries responsibility. Redact where possible. Document what data goes where. Provide opt-out and on-prem options when required by policy. Implement role-based approvals for actions.
Example: Redaction policy
- Hash user identifiers; keep consistent mapping for correlation.
- Truncate command lines; keep only executable and arguments relevant to detection.
Example: Governance artifacts
- Decision logs: who approved what, when, why.
- Allow/deny matrix: which tables, models, and actions are permitted per environment.
Testing and Validation
Test the agent like a product. Feed synthetic scenarios. Assert schema validity. Simulate API failures. Measure precision/recall against known datasets where possible.
Example: Unit tests
- Test that invalid JSON triggers a repair attempt.
- Test that unapproved tables are rejected.
- Test that time windows are enforced.
Example: Dry-run mode
- Replace "isolate" with "would_isolate=True" and log the action. Use for training and audits.
Deployment Patterns
You can ship this agent as a CLI tool, a small web service, or a serverless function. Start local, then containerize. Add observability and secrets management as you go.
Example: Local → Container
- Local dev with .env and virtualenv.
- Dockerfile with minimal base image, non-root user, mounted config.
Example: Serverless
- Wrap the agent in a function that triggers on a message queue (new alert) and posts the human-readable result to a chat channel with approve/deny buttons.
Implications and Applications (Where This Goes Next)
- Education and Training: This framework is your blueprint. Blend Python, APIs, AI, and cloud security into one cohesive skill stack.
- SOC Operations: Automate high-volume, low-complexity triage. Free humans for advanced hunts and strategy.
- Policy and Governance: Define action scopes, cost controls, human-in-the-loop procedures, and data handling policies.
Example: Fleet of agents
- One agent per log domain (identity, endpoint, network), coordinated via a message bus.
- A routing agent assigns tasks and aggregates conclusions.
Example: Continuous improvement loop
- Capture false positives, feed back into prompts and table instructions.
- Adjust allow lists and thresholds based on post-incident reviews.
Recommendations by Role
- For Cybersecurity Professionals: Learn Python basics, API auth, and LLM interaction. Get hands-on with a SIEM and build small proof-of-concepts.
- For Security Institutions: Pilot automation for repetitive tasks; invest in upskilling; set clear governance before enabling actions.
- For Students: Combine programming, KQL, and cloud security. Practice with real logs in a safe sandbox.
Example: 30-day plan
- Week 1: Python + API calls
- Week 2: KQL + log schemas
- Week 3: LLM prompts + JSON schemas
- Week 4: Wire it together + one remediation
Hands-On Labs (Do These to Lock It In)
Lab 1: Intent Parser
- Build derive_query_plan() with allow lists and JSON output. Test five user prompts.
Lab 2: KQL Filters
- Write three KQL queries for SigninLogs, DeviceLogonEvents, DeviceProcessEvents. Return only minimal fields.
Example: DeviceProcessEvents KQL
DeviceProcessEvents
| where Timestamp > ago(24h)
| where FileName in ("net.exe","wmic.exe","powershell.exe")
| project Timestamp, DeviceName, InitiatingProcessAccountName, FileName, ProcessCommandLine
Lab 3: Cognitive Hunt
- Create the analysis prompt with table-specific guidance and a JSON schema. Validate outputs with json.loads().
Lab 4: Remediation Dry-Run
- Implement isolate_device() with a dry-run flag. Confirm that actions log correctly.
Example: Dry-run wrapper
def maybe_isolate(host, confidence, dry_run=True):
if confidence == "high":
print(f"[DRY RUN] Would isolate {host}")
else:
print("Monitoring only")
Threat Hunting Tactics (Heuristics You'll Use Often)
- Credential Attack Signals: many failures then a success; unusual ASNs; new MFA patterns.
- Lateral Movement: new admin sessions, remote service creation, WMI, SMB session anomalies.
- Persistence: new autoruns, scheduled tasks, registry run keys, service changes.
- Exfiltration: large data transfers, rare destinations, odd hours, new protocols.
Example: Lateral movement KQL
DeviceLogonEvents
| where Timestamp > ago(24h)
| where LogonType in ("RemoteInteractive","NewCredentials")
| summarize Hosts=count(), DistinctHosts=dcount(DeviceName) by AccountName
| where DistinctHosts > 5
Example: Impossible travel
SigninLogs
| where TimeGenerated > ago(24h)
| project TimeGenerated, UserPrincipalName, Location
| summarize makeset(Location) by UserPrincipalName
| where array_length(makeset_Location) > 1
Human-in-the-Loop: Where You Stay in Control
AI makes suggestions, you make decisions. Use confidence thresholds and approval prompts for high-impact actions, and document outcomes to improve the system.
Example: Confidence gate
- confidence == high → prompt for isolate
- confidence == medium → escalate for manual review
- confidence == low → log and watch
Example: Explainability
- Always show rationale and the minimal evidence used for the decision (IP, counts, timestamps). Short, auditable, and human-readable.
Error Handling, Retries, and Fallbacks
Optimize for resilience. Your agent will hit rate limits, token overflows, malformed JSON, and flaky network calls. Plan for this upfront.
Example: JSON repair pass
- If json.loads() fails, call a "repair JSON" prompt with the raw output and schema; if it fails again, fallback to a minimal schema.
Example: SIEM query fallback
- If a query times out, narrow the timeframe by half and try again; if it still fails, notify the user to refine their request.
Security Considerations (Because You're Building Security Software)
- Secrets management: Never hardcode keys. Use a vault or environment variables.
- Principle of least privilege: API permissions should be scoped to the minimum required.
- Audit logging: Track who triggered actions and why.
- Data minimization: Don't send more to the LLM than necessary.
Example: Secrets pattern
import os
OPENAI_API_KEY = os.getenv("OPENAI_API_KEY")
if not OPENAI_API_KEY:
raise RuntimeError("Missing OPENAI_API_KEY")
Example: Action audit log
{ "timestamp": "…", "action": "isolate", "host": "Windows-Target-1", "approved_by": "analyst@org", "reason": "High confidence T1110" }
Extending the Agent: Multi-Agent Orchestration
Your single agent can grow into a fleet. One agent routes, another hunts identity, another hunts endpoint, and a fourth handles action planning. Start simple, then expand.
Example: Router agent
- Reads user request → picks which specialized agent to engage (identity vs endpoint vs cloud).
- Aggregates outputs into a single report.
Example: New action packs
- Revoke refresh tokens for a user.
- Add a temporary firewall block for a malicious IP with auto-expiry.
Authoritative Points to Remember
- An agentic AI can operate 300-500 times faster than a human at initial triage when correctly configured.
- The future of security operations will involve orchestrating multiple agentic AIs.
- Tokens are the billing unit. Both prompts and responses consume tokens. Cost control is design, not an afterthought.
Example: Speed leverage
- A user-to-report loop that took hours can be cut to minutes: intent in seconds, KQL in seconds, LLM analysis in seconds, and a decision in a minute or two.
Example: Structured or nothing
- If it's not valid JSON, it's not actionable. Enforce response_format and validate every time.
Practice Questions (Self-Check)
Multiple Choice:
1) What's the primary purpose of the first LLM call?
- C: Transform the user's natural language request into structured query parameters.
2) Why filter with KQL before sending to the LLM?
- B: Reduce tokens, manage API costs, and respect model limits.
Short Answer Prompts:
- Difference between system message and user message?
- Three guardrails and their purpose?
- Why is JSON preferred over plain text in this workflow?
Discussion Prompts:
- Risks of over-reliance without human oversight?
- Steps to add "disable user" capability?
- How to debug wrong-table selections in the intent prompt?
Common Pitfalls (And How to Avoid Them)
- Overly broad queries → Token blowups. Fix: pre-aggregate with KQL; narrow fields and time.
- Unstable outputs → Inconsistent parsing. Fix: rigid JSON schema + response_format + validation + repair pass.
- Premature autonomy → Risky actions. Fix: confidence thresholds, approvals, rollback plans.
- Hallucinated tables/actions → Unexpected behavior. Fix: strict allow lists checked in code.
Example: Parsing guard
try:
data = json.loads(findings)
except json.JSONDecodeError:
findings = repair_json(findings, schema)
Tips and Best Practices
- Write prompts like contracts. Be explicit, short, and firm about output format.
- Keep log records small but meaningful. Time, principal, action, result, host, IP.
- Review and tune after every incident. What confused the agent? Fix it in prompts and allow lists.
- Start with read-only mode, then graduate to actions behind approval gates.
Example: Prompt hardening
- "If uncertain, return 'confidence': 'low', and include 'rationale' with what additional data is needed."
End-to-End Example: From Prompt to Isolation
1) User: "Check for suspicious logons to 'Windows-Target-1' in the last 48h."
2) Intent LLM returns: table=DeviceLogonEvents; timeframe=48; entities.host=Windows-Target-1.
3) KQL fetch returns summary of failures/successes by hour and IP.
4) Cognitive LLM flags high-confidence credential spraying (T1110) with IOCs.
5) Agent asks for approval to isolate; analyst approves.
6) Agent calls Defender API: token → device ID → isolate. Logs the action and notifies the team.
Example: Analyst-facing summary
- Threat: Credential Spraying (T1110)
- Host: Windows-Target-1
- Evidence: 17 IPs, 200+ failures, 1 success, off-hours
- Action: Host isolated (ticket #12345)
Why This Skill Stack Matters
The SOC role is evolving. Instead of clicking through dashboards, you'll design intelligent systems to triage, analyze, and act at scale. Python + APIs + AI + KQL is that stack. This course gave you the blueprint and the building blocks,use them to ship a working agent, then push it further.
Conclusion: What to Do Next
You now have a comprehensive model for building an AI-powered SOC analyst: a clear architecture, a two-call LLM workflow, solid guardrails, cost controls, structured outputs, and a working path to automated remediation.
Key takeaways:
- Agentic AI is about action, not just insight. The loop closes when JSON findings trigger safe, auditable responses.
- Prompt engineering, KQL precision, and strict schemas are your quality levers.
- Guardrails and governance make this deployable in real environments, not just demos.
- Cost and token management must be baked into the design.
Next steps: implement the minimal agent end-to-end, even if it's rough. Dry-run actions, iterate on prompts, and improve table-specific instructions. Add one remediation you can trust, then grow your library. Over time, you'll graduate from "analyst" to "orchestrator," from chasing alerts to engineering intelligent systems that protect your environment at machine speed.
Final nudge:
Build the first version this week. Keep it lean. Make it safe. Then ship small improvements daily. Your future self,the one running a fleet of reliable security agents,will thank you.
Frequently Asked Questions
This FAQ is a practical reference for anyone evaluating, building, or managing an AI-driven cybersecurity program with Python and agentic AI. It covers core concepts, setup, model usage, prompt design, cost control, security guardrails, deployment patterns, and real examples of threat hunting and automated remediation. Use it to answer quick questions, align teams, and make sound decisions without getting lost in jargon.
Section 1: Fundamental Concepts
What is Agentic AI in cybersecurity?
Agentic AI is autonomous security work with checks and context.
It's more than scripts. These agents interpret plain English, choose data sources, run targeted queries, analyze results, and take action when rules permit. Think of an "AI SOC Analyst" that hears "Suspicious logins on finance servers," determines the right tables, composes KQL, analyzes failed logons and lateral movement, and proposes isolation if risk is high.
Why it matters:
It compresses the time between signal and action. Repetitive Tier 1 tasks move faster, while humans handle judgment calls and complex investigations.
Real-world example:
An agent collects DeviceLogonEvents for a named host over the last 24 hours, detects a burst of failed logins from a new geolocation, correlates it with successful access from the same IP, and drafts a report with MITRE technique mappings and next-step actions,optionally triggering machine isolation behind an approval gate.
Why is AI becoming critical for cybersecurity roles?
Volume, velocity, and variability of signals exceed human bandwidth.
Security teams face sprawling telemetry across endpoints, identity, SaaS, and cloud. AI can correlate millions of events in minutes and surface patterns people miss.
What changes for teams:
- Automation of Tier 1 triage and enrichment
- Faster hypothesis testing during hunts
- Continuous monitoring at scale
Business impact:
Shorter mean time to detect and respond, lower alert fatigue, and clearer executive reporting. Analysts shift focus toward high-value investigation and control design. For example, AI can summarize 50K sign-in records into three clear risk narratives with confidence levels and suggested actions, which a human then verifies and executes if appropriate.
What is ChatGPT and how does it differ from a search engine?
ChatGPT synthesizes; search engines index.
A search engine points you to links. ChatGPT reasons over your prompt, follows instructions, and produces a formatted output,reports, code, or JSON. It can adopt a role ("Act as a SOC lead"), work with your data, and iteratively refine results.
In agents:
ChatGPT acts as the "brain" for interpretation and analysis. Example: It translates "Check for impossible travel for user A in the last day" into a structured query plan, ingests filtered logs, and returns a machine-readable threat assessment with confidence and evidence.
Practical benefit:
Less time jumping across tabs and more time making decisions. The agent asks better questions of your data and produces consistent, reviewable output.
What is prompt engineering?
Prompt engineering is instruction design that drives reliable outputs.
Good prompts set role, constraints, examples, and output format. For security, that means specifying the table, fields of interest, known false positive patterns, and the exact JSON schema for the result.
Example:
"Analyze these DeviceLogonEvents for brute force indicators. Focus on repeated failures followed by success from the same IP. Exclude expected admin ranges. Return JSON: {title, description, confidence, indicators[], recommended_actions[]}."
Outcome:
Predictable, scannable outputs you can validate and pass to other systems. Better prompts reduce cost, errors, and rework.
Section 2: Python and Development Environment
Why is Python the chosen language for this project?
Python balances speed to value with a rich ecosystem.
It's easy to read, has strong community support, and integrates well with APIs, data frames, and cloud SDKs. For this use case: the OpenAI client for LLM calls, pandas for log shaping, and Azure SDKs for KQL queries fit together cleanly.
Result:
Shorter development cycles, simpler debugging, and easier handoffs between engineers and analysts. You can quickly scaffold an agent, iterate on prompts, and ship improvements without heavyweight tooling.
What is the goal of learning Python for building an AI agent?
Target "code modification" competence, not perfection.
Be able to read existing scripts, change parameters, swap models, add fields, and handle errors. Write small utilities to parse JSON, call APIs, and format reports.
Practical scope:
- Understand functions, loops, and dictionaries
- Parse/produce JSON reliably
- Add guardrails and logging
Why this level is enough:
With these skills, you can co-develop with AI assistants, test ideas quickly, and maintain a production-worthy agent without becoming a full-time software engineer.
What is needed to set up the development environment?
Three parts: Python, VS Code, and core extensions.
- Install Python and ensure it's on PATH
- Install Visual Studio Code
- Add extensions: Python (linting/debugging) and Black (formatting)
Why this stack:
Fast feedback, integrated terminals, and consistent formatting reduce friction. Pair it with a virtual environment and a requirements.txt to keep dependencies clean. This keeps your agent reproducible and easy to share across the team.
What is a Python dictionary and why is it important here?
Dictionaries map keys to values; they mirror JSON.
Most agent outputs are JSON that your Python code reads as dictionaries. Example: {"title":"Brute force detected","confidence":"high"}. You'll access fields like result["confidence"] and loop over arrays of indicators.
Benefit:
Seamless handoff from model output to logic that drives actions, dashboards, or tickets. Fewer parsing mistakes and faster development.
What is JSON and its role in API communication?
JSON is the lingua franca between your agent and services.
It's human-readable and easy to parse in code. The model returns findings in JSON; Python converts that into dictionaries for validation and action.
Why it matters:
Predictable structure enables automation. For example, the agent can read confidence, affected hosts, and recommended actions directly from JSON, then decide whether to request human approval or call a remediation API.
Section 3: Interacting with the OpenAI API
How does the Python code connect to the OpenAI API?
Install the library, authenticate, then call.
- pip install openai
- Create a client with your API key (use environment variables or a secrets manager)
- Send messages with your system/user prompts and parameters
Example flow:
Compose a system role ("You are a cyber threat hunter"), add user context, request JSON output, and handle the response. Wrap calls in try/except to manage timeouts or rate limits gracefully.
Certification
About the Certification
Get certified in Agentic AI SOC Threat Hunting with Python. Prove you can turn plain-English requests into KQL queries, map findings to MITRE ATT&CK, auto-isolate hosts via API, and build guardrailed automation that cuts alert-chasing.
Official Certification
Upon successful completion of the "Certification in Building and Deploying Python Agentic AI for SOC Threat Hunting", you will receive a verifiable digital certificate. This certificate demonstrates your expertise in the subject matter covered in this course.
Benefits of Certification
- Enhance your professional credibility and stand out in the job market.
- Validate your skills and knowledge in cutting-edge AI technologies.
- Unlock new career opportunities in the rapidly growing AI field.
- Share your achievement on your resume, LinkedIn, and other professional platforms.
How to complete your certification successfully?
To earn your certification, you’ll need to complete all video lessons, study the guide carefully, and review the FAQ. After that, you’ll be prepared to pass the certification requirements.
Join 20,000+ Professionals, Using AI to transform their Careers
Join professionals who didn’t just adapt, they thrived. You can too, with AI training designed for your job.